Background:
A large enterprise company in the pharmaceutical sector has been using AWS for some time now for a number of key workloads.
Special care is taken around the security of the environment due to the high stakes around the manufacturing process, the intellectual property held by the company, private user information (especially around experiments and protected healthcare information), etc. aAs more teams create AWS accounts and as more workloads are deployed, there’s a concern of a potential misconfiguration that will lead to compromise.
Last week a development EC2 instance was compromised. An older, unused Security Group was attached to the EC2 instance by mistake with a configuration that allowed traffic from all IP’s on all ports to reach the EC2 instance.
While a broader set of tools is implemented to prevent this from happening, there’s an urgent need to inspect all AWS accounts in the organization for the presence of such Security Groups.
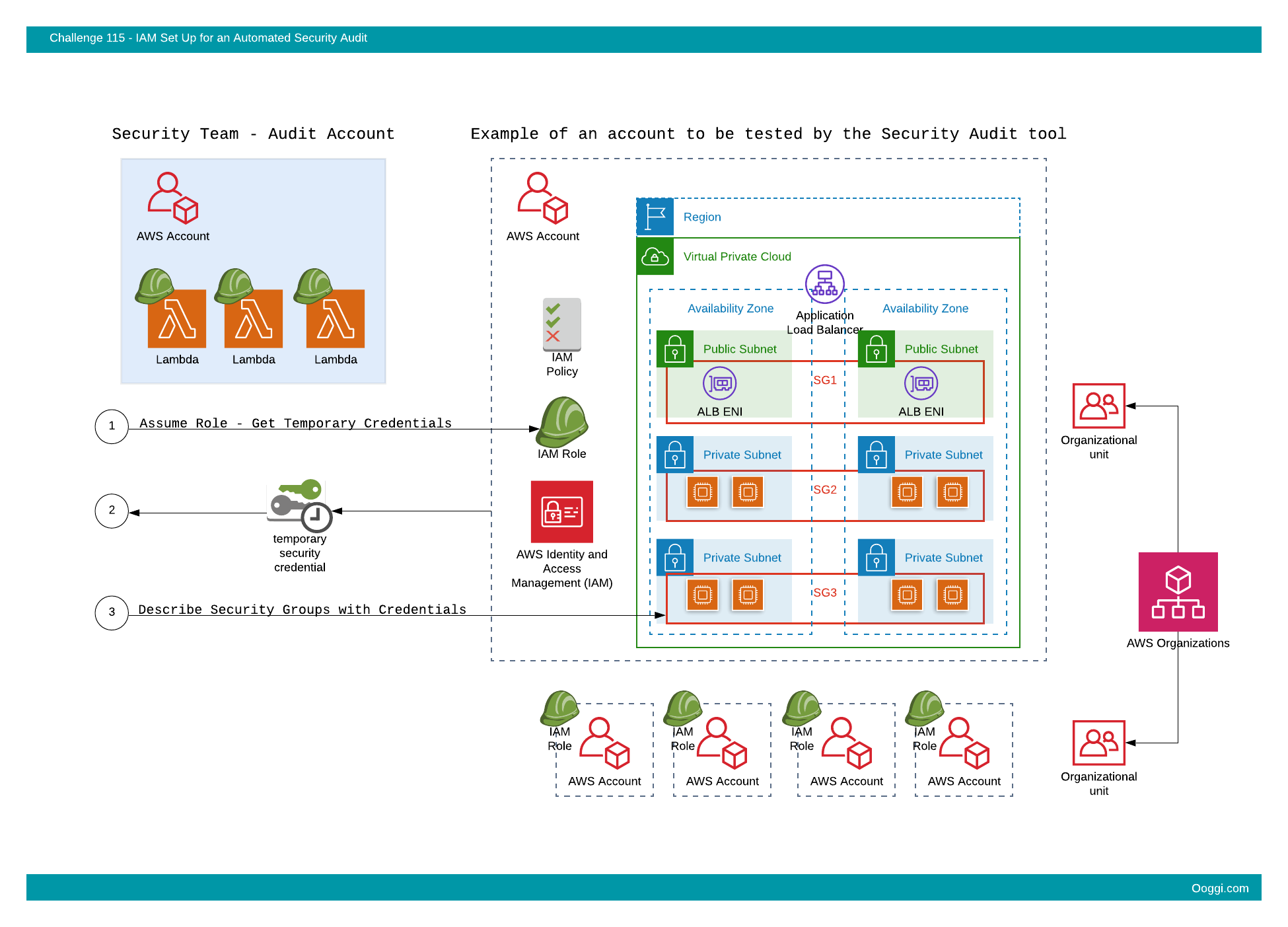
An ad-hoc script was put together, but there’s still a need to set up authentication and authorization in a way to allow the “Security Account” (the account in which the tool will be running) to access project/team AWS accounts and call the relevant EC2 API’s for inspection.
Bounty:
- Points: 20
- Path: Cloud Engineer
Difficulty:
- Level: 2
- Estimated time: 1-2 hours
Deliverables:
- A set of temporary credentials (Access Key, Secret Key, Token) that will allow the inspection of a remote AWS account
Prototype description:
IAM Roles and policies should be configured with the principle of least privilege in mind. Once these are in place, temporary AWS credentials should be created to allow the caller to describe the EC2 Security Groups across the account.
The credentials will be passed on security to the team and the test will be executed.
If all works well, this setup will be replicated to other AWS accounts in the organization to facilitate a broader inspection.
Requirements:
-
A set of active temporary credentials shall be provided which include an AWS Access Key, Secret Key and Session Token. For Example:
Access Key ID:AKIAIOSFODNN7EXAMPLE
Secret Access Key:
wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
Session Token:
AQoDYXdzEPT//////////wEXAMPLEtc764bNrC9SAPBSM22wDOk4x4HIZ8j4FZTwdQWLWsKWHGBuFqwAeMicRXmxfpSPfIeoIYRqTflfKD8YUuwthAx7mSEI/qkPpKPi/kMcGdQrmGdeehM4IC1NtBmUpp2wUE8phUZampKsburEDy0KPkyQDYwT7WZ0wq5VSXDvp75YU9HFvlRd8Tx6q6fE8YQcHNVXAkiY9q6d+xo0rKwT38xVqr7ZD0u0iPPkUL64lIZbqBAz+scqKmlzm8FDrypNC9Yjc8fPOLn9FX9KSYvKTr4rvx3iSIlTJabIQwj2ICCR/oLxBA==
- The temporary credentials shall not be valid for longer than 30 minutes.
-
The provided credentials shall provide to a calling application with the following permission:
ec2:DescribeSecurityGroups
-
An API call to describe Security Groups in the Ireland (eu-west-1) region shall uncover at least one Security Group with a name prefixed by:
ooggi-sg-test
For example:
ooggi-sg-test-my-sg
- The Security Group can be created in any VPC as long as the region is the Ireland (eu-west-1) region.
- Any other API call using the provided temporary credentials (besides ec2:DescribeSecurityGroups) shall fail with the appropriate error response from the AWS API.
Your mission, if you choose to accept it,
is to set up AWS IAM to allow a remote application to inspect the Security Group configuration of an AWS account.